The scope of this article is to describe the steps required to configure SSL for Nagios XI and to force SSL with a permanent redirection. In this example, I have made the assumption that certificate files have been generated and in this example I will be using the hostname ‘nagios.dean.local’ for my Nagios XI server throughout the configuration steps.
In order to configure SSL version 2011R1.6 or later of Nagios XI is required to ensure all of data is displayed correctly in Nagios XI interface. The installation of Nagios XI should install the required SSL components, to verify this run the following command on the Nagios XI server.
sudo yum install mod_ssl openssl -y
Also, you will need to ensure that inbound connectivity on TCP service port 443 for the https protocol is permitted. If this is not the case we can create input chain to accept connections.
sudo iptables -I INPUT -p tcp --dport 443 -j ACCEPT sudo service iptables save
Prior to configuring SSL for Nagios XI we will create a backup of the configuration files which will modify as part of this process in case we are required to revert the changes. The SSL certificate files will need to be available NagiosXI server, place the certificate file in ‘/etc/pki/tls/certs’ and the key file in ‘/etc/pki/tls/private’.
sudo cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.backup sudo cp /etc/httpd/conf.d/ssl.conf /etc/httpd/conf.d/ssl.conf.backup sudo cp /etc/httpd/conf.d/nagiosxi.conf /etc/httpd/conf.d/nagiosxi.conf.backup sudo cp /usr/local/nagiosxi/html/config.inc.php /usr/local/nagiosxi/html/config.inc.php.backup
Once the certificate and key files have been copied to the locations we need to configure the httpd service by modifying the file ‘/etc/httpd/conf.d/ssl.conf’
SSLCertificateFile /etc/pki/tls/certs/nagios.dean.local.crt SSLCertificateKeyFile /etc/pki/tls/private/nagios.dean.local.key
Also, we will need to configure the virtual host to listen to requests on TCP server port 443 for the https protocol by modifying the file ‘/etc/httpd/conf/httpd.conf’.
NameVirtualHost *:443
Once the file has been modified we will restart the ‘httpd’ service to apply the configuration. We may verify the connection to the server by browsing to the server, in this example https://nagios.dean.local.
sudo service httpd restart
Now we will need to edit ‘/usr/local/nagiosxi/html/config.inc.php’ and modify the below line to which the value by default should be configured as ‘false’.
$cfg['use_https']=true;
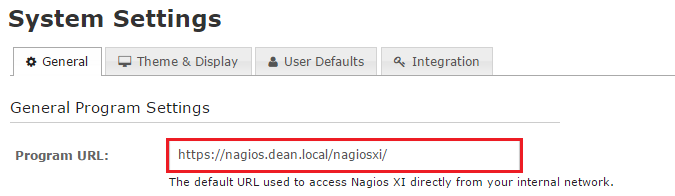
Now browse to the Nagios XI web interface and browse to Admin > System Settings and modify the program URL value to contain the https protocol instead of http and select ‘Update Settings‘. For Example https://nagios.dean.local/nagiosxi.
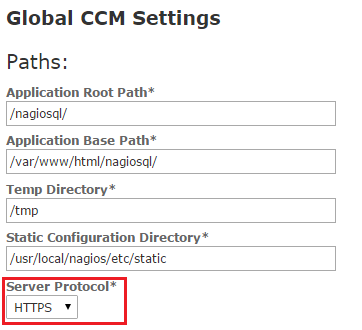
Next, browse to ‘Configure > Core Config Manager > Config Manager Admin > Config Manager Settings’ and modify the Server Protocol value to be https and select ‘Save‘.
Finally, we will need to edit the file ‘/etc/httpd.conf.d/nagiosxi.conf’, which by default should be similar to the below:
# NameVirtualHost * :443 <VirtualHost *:80> <Directory "/usr/local/nagiosxi/html"> #SSLRequireSSL Options None AllowOverride None Order allow, deny Allow from all # Order deny,allow # Deny from all # Allow from 127.0.0.1 # AuthName "Nagios XI" # AuthType Basic # AuthUserFile /usr/local/nagiosxi/etc/htpasswd.users # Require valid-user </Directory </VirtualHost>
We now will add the following to configuration file to enable the virtual host to listen on HTTPS and specify the path to the certificate files that been generated.
<VirtualHost *:443> SSLEngine on SSLCertificateFile /etc/pki/tls/certs/nagios.dean.local.crt SSLCertificateKeyFile /etc/pki/tls/private/nagios.dean.local.key <Directory "/user/local/nagiosxi/html"> AllowOverride All </Directory> </VirtualHost> Alias /nagiosxi "/usr/local/nagiosxi/html"
To force SSL with a permanent redirection the following will be required to be added between ‘<VirtualHost>’ and ‘</VirtualHost>’ tags and add the configuration for the rewrite engine between the start and end tags for the virtual host listing on TCP service port 443.
Redirect permanent / https://nagios.dean.local
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule nagiosxi/api/v1/(.*)$ /usr/local/nagiosxi/html/api/v1/index.php?request=$1 [QSA,NC,L]
</IfModule>
Once saved, the updated configuration file ‘/etc/httpd.conf.d/nagiosxi.conf’ should look similar to the below:
# NameVirtualHost * :443
<VirtualHost *:80>
<Directory "/usr/local/nagiosxi/html">
#SSLRequireSSL
Options None
AllowOverride None
Order allow, deny
Allow from all
Redirect permanent / https://nagios.dean.local
# Order deny,allow
# Deny from all
# Allow from 127.0.0.1
# AuthName "Nagios XI"
# AuthType Basic
# AuthUserFile /usr/local/nagiosxi/etc/htpasswd.users
# Require valid-user
</Directory
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/nagios.dean.local.crt
SSLCertificateKeyFile /etc/pki/tls/private/nagios.dean.local.key
<Directory "/user/local/nagiosxi/html">
AllowOverride All
</Directory>
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule nagiosxi/api/v1/(.*)$ /usr/local/nagiosxi/html/api/v1/index.php?request=$1 [QSA,NC,L]
</IfModule>
</VirtualHost>
Alias /nagiosxi "/usr/local/nagiosxi/html"
This completes the configuration steps required to force SSL with a permanent direct for the Nagios XI server. In my example, I would verify the connection to browsing to ‘http:\\nagios.dean.local\nagiosxi’ which should redirect to ‘https:\\nagios.dean.local\nagiosxi’. The configuration files that are required be modified can be found as examples at the following link.